Find Out What HIPAA Risk Assessment Is and Its Procedure
HIPAA security risk analysis
Data breaches are nothing new. They have become much more common since the use of electronic medical records. Keeping this in mind, a security assessment is a critical tool for detecting vulnerabilities and threats to Protected Healthcare Information (PHI).
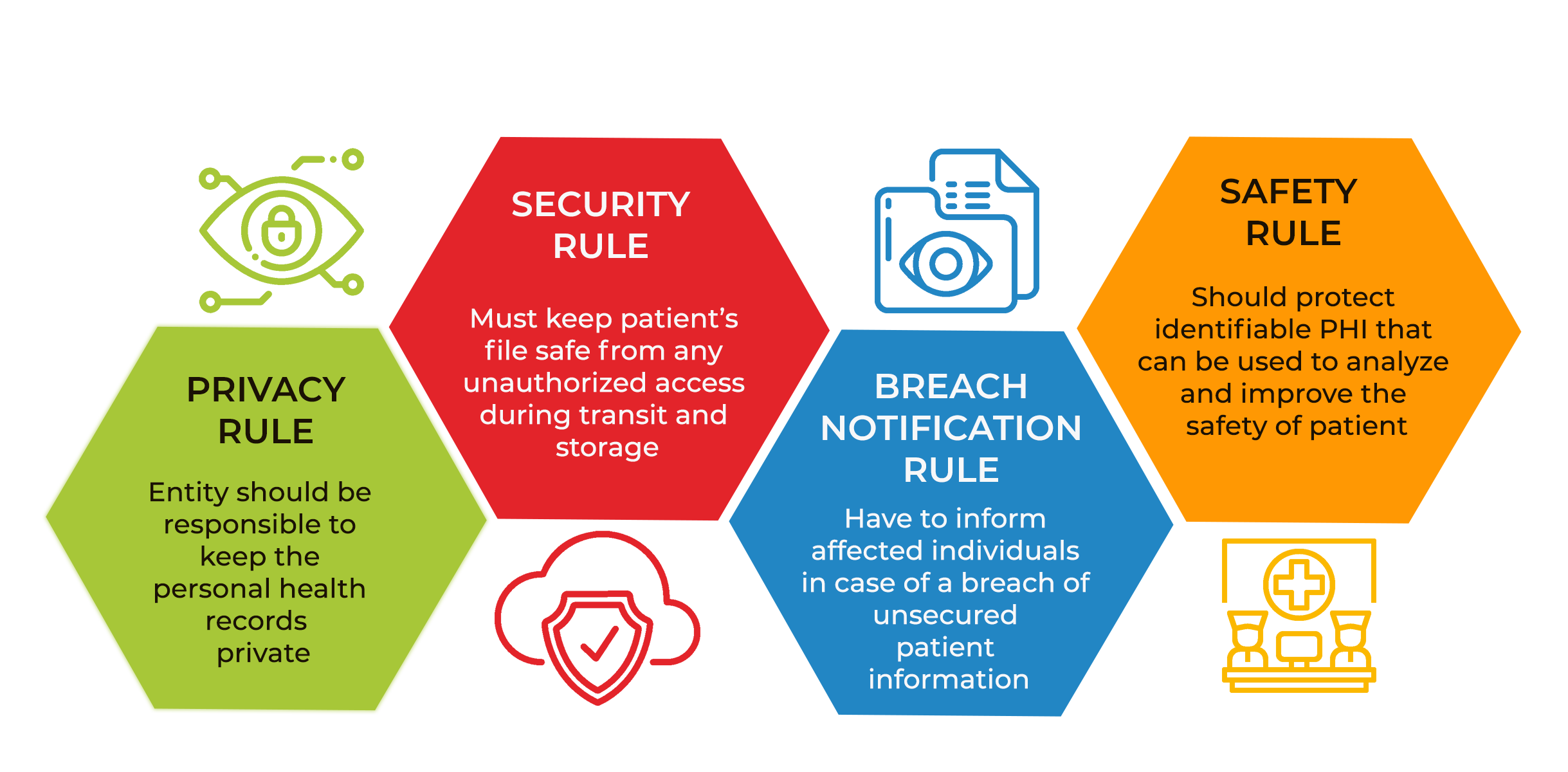
A risk analysis is not only useful for detecting hazards; it is also mandated by the HIPAA Security Rule, which requires insured companiesand their business partners to conduct an annual HIPAA risk assessment and implement security measures to protect PHI.
Get to Know What is HIPAA Security Risk Assessment
Companies must understand what categories of PHI they may need to access, where vulnerabilities and safety concerns exist, and what might endanger the confidentiality and reliability of PHI before implementing safeguards. HIPAA security risk analysis and conformance necessitate a complete risk assessment to identify and report weaknesses in their operations by covered firms and their business associates.
A risk assessment not only identifies potential risks and weaknesses, but it also enables you to take the necessary steps to protect PHI, potentially saving your company from severe penalties.
What Are the Steps Followed in HIPAA Security Risk Analysis?
Step 1: Ascertain the PHI you want to access
Examine where your firm would retain ePHI. What mechanism is used to transmit that data? This information may be gained by reviewing the previous or recent projects, conducting personnel interviews, and reviewing documents from previous risk assessments.
Step 2: Assess your ongoing security measures
Examine and assess your existing security policies once you've reviewed where ePHI is stored at your company and what technologies are used to reach, interpret, and safeguard the data. Begin by recording your organization's existing efforts to safeguard PHI.
Step 3: Ascertain the area of vulnerability
Consider the weaknesses in your entity's defenses and the possibility of potential threats to ePHI that might threaten the integrity and security of ePHI stored by your organization, armed with the information you've gathered thus far.
Step 4: Figure out your risk tolerance
Assign risk ratings to any risks and security vulnerabilities uncovered during your firm's HIPAA security risk evaluation. The degree of risk is computed by calculating the likelihood of all known hazards and effect combinations. The allocated exposure to risk is the highest when a hazard is anticipated to occur that will have a significant impact on the organization.
Step 5: Prepare the documents
You must record everything and finalize your document so that it clearly outlines the PHI with which you work, the security gaps or vulnerabilities, and the steps you take to reduce threats to ensure PHI security.
Covered organizations need to ensure that they run adequate HIPAA security risk analysisto make sure PHI is protected.