What Are Vulnerability Assessment Services and What Do They Include?
Vulnerability Assessment Services
With the increasing Internet penetration in the industrial and business sectors, organizations today can easily have a significant online presence. They can identify potential clients for their goods and services, as well as inexpensively get raw materials from any provider located everywhere.
The Internet has benefitted the majority of people, but it has also raised the possibility of criminal intruders stealing personal data and money. Cybercriminals are continually looking for flaws in software, systems, or networks to steal a company's assets and private data.
To secure its data, a firm must take the required steps to discover security risks and defects and take corrective action. You may detect and repair security issues with vulnerability assessment and penetration testing or VAPT services. A vulnerability is defined as a programming fault, a defect, or a systemic weakness that may be exploited to hack into a system network or server.
VAPT allows you to review system components to find security defences, as well as conduct a vulnerability assessment of your system network or application. Vulnerability assessment is the initial step in discovering a defect or weak point in a system, network, or application. Penetration testing, on the other hand, aids in discovering the vulnerability.
You may obtain dependable vulnerability assessment services from reputable technological specialists that deliver exceptional outcomes. You should be familiar with vulnerability assessment approaches if you want to uncover security problems.
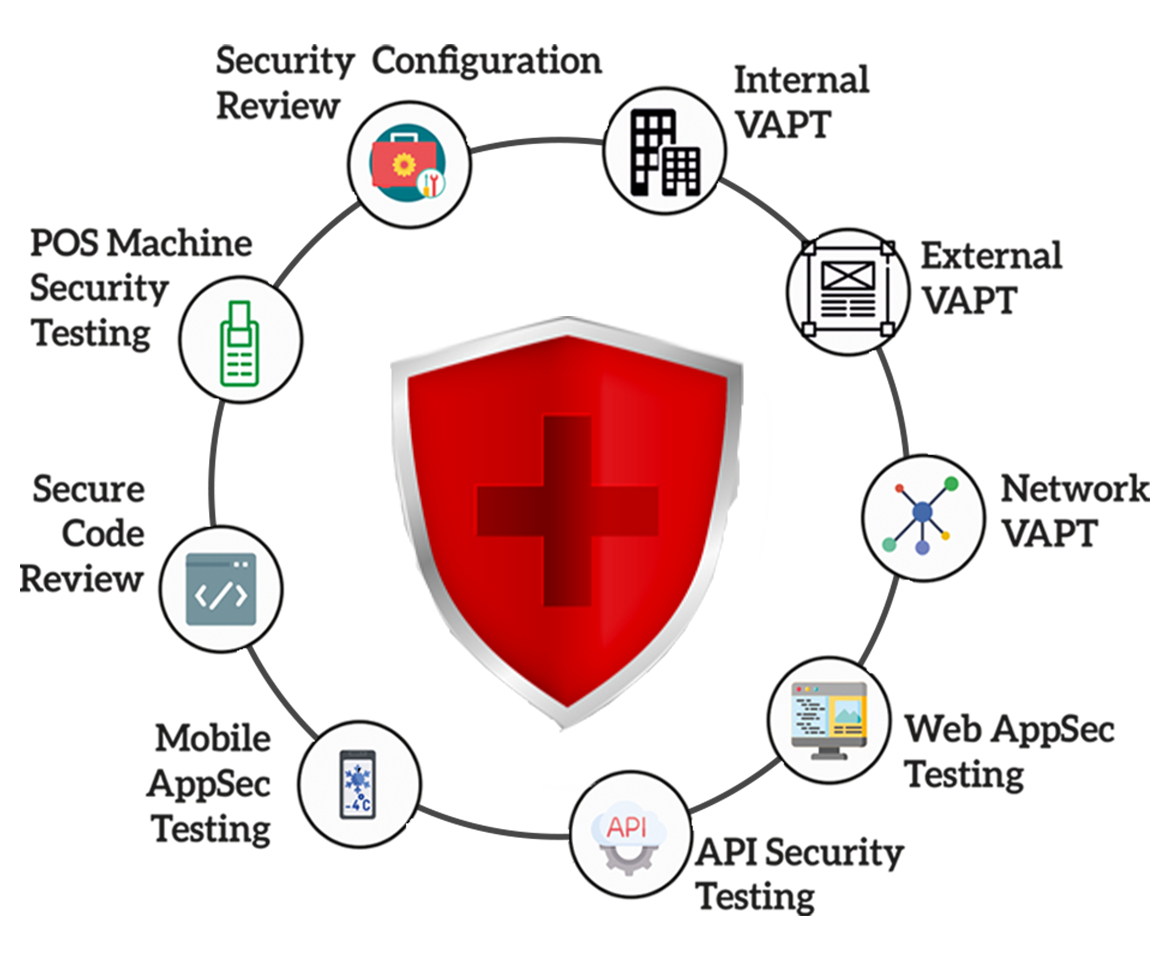
Know What Vulnerability Assessment Services Include
Because hackers employ a wide range of tools, tactics, and strategies to breach security systems and networks, a company's cyber security should be audited on a regular basis. You may obtain a full evaluation of your system application, a rigorous study of the hazards, and recommendations on how to address them by doing VAPT testing.
Your online store or business can meet the industrial security requirements required for GDPR assessment, PCI DSS certification, ISO 27001, or HIPAA evaluation. By working with a credible VAPT service provider, you may have managed services and system components analysis for vulnerabilities regularly to discover and reduce false positives.:
• System Infrastructure
Network: Reliable vulnerability assessment services will examine the effectiveness of your network security in terms of network access limitation, network segmentation, firewall deployment, and remote connectivity.
Email: They also examine the vulnerability of your email accounts to phishing and spam.
• Applications
Web applications: Front-end automated vulnerability scanning techniques or static/dynamic source code analysis are used to discover any security problems in web apps as well as their source code.
To check for security vulnerabilities or flaws in a mobile app, various mobile application scanning technologies are utilized.
It is examined as a desktop program to determine how data is delivered and managed.
If you want to secure your company's private data, make sure you employ the best vulnerability assessment services from a reputable source.
Some prerequisites for starting a vulnerability assessment or penetration test include connection, user credentials to access the program, IP whitelisting, and so on. You must complete these papers in accordance with the appropriate assessment and share the completed documents with the team to begin the exams.